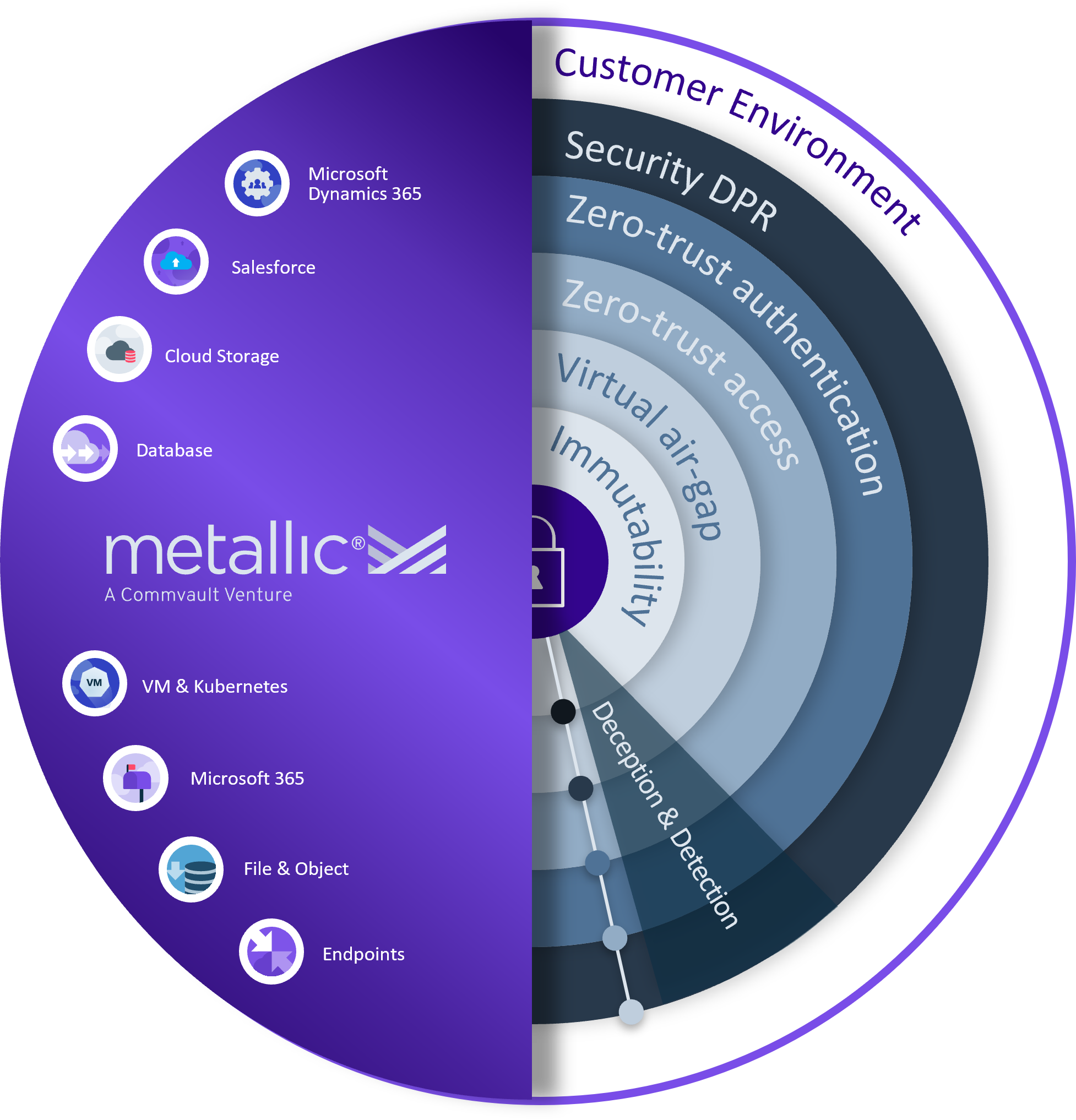
Deception technology is a must have and here is why
“Although to use deception in any action is detestable, nevertheless in waging war it is praiseworthy and brings fame: He who conquers the enemy by deception is praised as much as he who conquers them by force.”
– Machiavelli, Discourses on Livy
Deceptive technologies are not part of most companies’ cybersecurity portfolios because they’re seen as too risky from a legal standpoint, there isn’t enough budget available to implement them, or there is a lack of understanding about the state of deceptive technologies.
Deception can be used as part of an overarching data protection strategy to draw out attackers so they can be caught off guard. In this case, the goal is to make them commit to an action that leads them to believe they’re winning, only to find out later that they’ve made a fatal mistake. “Clausewitz” was a Prussian general who wrote a treatise called ‘On War’ (1832) during the Napoleonic Wars. He argued that war could not be won through sheer force alone; rather, it must be won through superior strategy, logistics, and morale—and he developed a system for analyzing these factors. His theory of warfare became known as “fog of war,” because he believed that no one could ever really see what was happening around him.
Cyber defense strategies can vary greatly depending upon the organization and environment. Some organizations may deploy a classic area defensive posture, where they attempt to prevent attacks through the use of firewalls, IPS devices, IDS systems, and other similar tools. However, if an attacker gains access to the network, then the next step would be to identify vulnerabilities and exploit them to damage your data. An example of this could be a SQL injection vulnerability, where an attacker attempts to gain control of a database server. Once the attacker gains control of the server, then the attacker can perform actions such as deleting data, modifying data, or even creating new accounts. To counter this, organizations should implement penetration testing services to ensure that no vulnerabilities exist within their system. Penetration testing allows organizations to test their security posture against known threats, so that they can determine what steps must be taken to secure their networks.
Deception is not just a tactic; it is an integral part of any security and data protection program. In order to deceive an attacker, one must first understand how they think. Once you know what your adversary thinks, then you can design a plan that will lead them down the path where you want them to go.
Tools for making the strategy successful should include:
- Agentless to ensure that attackers cannot determine that something is running.
- Reduces risk by preventing bypassing of security tools and diminishing supply chain risk.
- Zero-day protection that can detect malicious activity beyond signatures and can’t be leveraged as a pivot point when the tool is run.
There is only one product out there that really addresses this problem. It’s called ThreatWise™ by Metallic®. It’s a fully integrated data protection solution, that safeguards your crown jewels before you’re compromised.
Visit metallic.io to learn more.