Beyond Perimeters: A Holistic Approach to Data Protection in the Cloud
A New Cybersecurity Imperative
From ransomware-as-a-service toolkits to the rise of double and triple extortion tactics, cyberattacks look different these days. While exploiting and monetizing valuable data is still the endgame, motives have evolved – posing significant risks to economic, public, and national well-being.
To address these new and complex data security challenges, on March 2nd, 2023, the White House announced a new National Cybersecurity Strategy aimed at reimaging (and rearchitecting) national cyber defense methodologies. At the forefront of this strategy is the investment in next-generation technologies that fortify cyberspace defense capabilities and promote the privacy and securing of data.
Knowing the critical, and interconnected, role data protection plays in overarching security and cyber recovery strategies, the security posture of your data protection vendor has never been more important. The following blog details how Metallic’s multi-layered detection, protection, and response capabilities keep data safe (and recoverable) while delivering proven resiliency in the cloud.
Security Posture Management
Security posture management programs, at its core, define how to protect and fortify networks, information, and systems, while continuously identifying and remediating risks. It is the lifeblood of any security program and is front and center in how companies think about, invest in, and implement security protocols and measures.
Metallic maintains a best-in-class security posture management program based on NIST 800-53v5 security guidelines. In addition to meeting NIST cybersecurity procedural standards, our commitment to security and compliance across our cloud data protection solutions is demonstrated by the many industry-leading data sovereignty, privacy and security certifications, attestations and validations by third parties, including: our achievement of compliance with FedRAMP High In Process – In PMO Review status, GDPR, CJIS, FIPS 140-2, HIPAA, ISO 27001:2013m PCIDSS, SOC 2 Type II and successful DoD Impact Level 5 assessments. We also comply with FIPS 140-3 cryptographic requirements as validated by an accredited 3rd party and have already submitted our documentation for review and approval by NIST. To date, Metallic is the only Data Protection as a Service offering to achieve FedRAMP High and DoD IL5 status.
Secure by Design
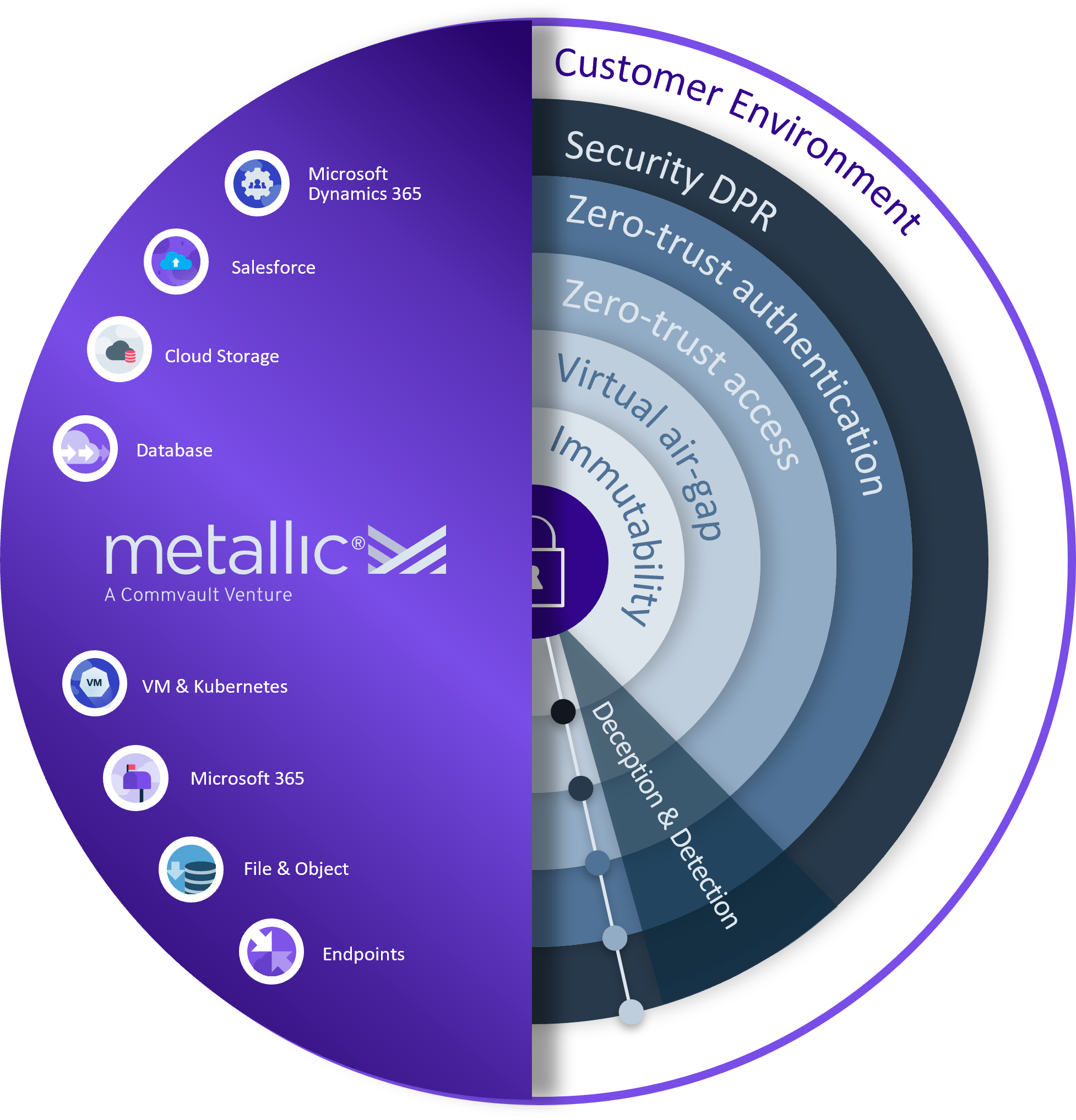
It’s critical to understand that security isn’t just about deploying a bunch of tools in the cloud at the perimeter, and calling it done. Security-in-depth can’t be an afterthought but needs to be throughout every aspect of an organization’s actions – from their webpage, to their email, and beyond. It must layer across all products, services, and the entire supply chain (on premise and in the cloud) – as well as the individuals who interface with these specific touchpoints. Commvault’s security in-depth approach offers comprehensive protection of our customers’ crown jewels (their data), employing a multi-layered security for detection, protection and response threats across all layers of Metallic SaaS offerings.
The People
Security isn’t the responsibility of the IT security team – it’s EVERYONE’s responsibility – and the weakest link is the human factor. It starts with an individual employee. Which is why Commvault thoroughly evaluates, screens, hires, and trains the right talent to ensure stringent adherence with security processes. The Metallic platform itself is deployed in the cloud and is managed by highly skilled and experienced DevSecOps and Site Reliability Engineers.
The Process
Significant investments have been made to harden the Metallic cloud environment using next generation cloud native threat detection, protection and response capabilities including EDR (Endpoint Detection and Response), NDR (Network Detection and Response), infrastructure and Web Application Firewalls, IDS (Intrusion Detection System), IPS (Intrusion Prevention System) and end-to-end service monitoring tools are deployed. AI based log analytics engines are also used to perform thorough automated security analysis of all service, audit and infrastructure logs and an advanced SIEM (Security Information and Event Management) service is implemented to ensure no critical event goes unaddressed.
The Code
A key, but often overlooked element, is the software code itself. Metallic security program starts with comprehensive security requirements built into the software code along with detailed code reviews, static and dynamic application security testing using next generation vulnerability scanning tools are baseline policies that every software developer at Commvault must abide by. Reviews and approvals based on security test results in dev, test, pre-prod environments are performed by different teams and no code with any critical, high or medium security vulnerabilities is ever released into production environment.
Zero Trust Control
Zero trust commonly relates to the general methodology of verification and access for users inside or outside a specified network. With Metallic, access, authorization, authentication and audit controls are implemented across the entire service using zero trust frameworks, in combination with least privileged model. Access is based on stringent Role Based Access controls with MFA (multi-factor authentication) and FIPS certified hardware tokens. All constructive or destructive actions require multiple reviews and approvals by the Metallic Change Control Board, Architecture Review Board and peer reviews via automated workflows. Advanced cloud based privileged identity management service is used to manage, monitor and audit all privileged access along with behavioral tracking services integrated with the SIEM for alerting and notification of anomalous behaviors.
Air-Gapped Architecture
Given the nature of cyber threats, a key requirement emerging around data storage and recoverability is the need for virtually air-gapping data copies. The concept of air-gapping has been used by organizations for years though with the introduction of cloud services, the key is in the implementation of Metallic.
Metallic is a truly virtually air-gapped solution, separate from customer network control boundaries, customer environments/datacenters/networks, and from Commvault’s internal network. Metallic is deployed on an independent security domain with dedicated access, authorization, authentication, audit and security services. Fully decoupled backup architecture results in isolated and immutable copies of customer data that’s inaccessible to threat actors within their network.
Secure data storage also requires significant controls (process, people and technical) implemented to prevent data tampering. All data is encrypted in transit within Metallic, while all data is stored with dual AES 256 bit encryption at rest, privacy locks, and advanced cloud features. This ensures accidental or malicious deletion protection and ultimately prevents any access to customer’s data in a readable format by a threat actor.
Rigorous Testing
Along with all the security controls, processes and procedures in place, a critical aspect of a good Security Program is regular and continuous vulnerability assessments. Metallic performs multiple internal and third-party assessments such as red teaming, threat hunting, Business Continuity and Disaster Recovery (BCDR) exercises to continually validate, assess and improve security of the Metallic platform.
Customer Control
At the end user level, Metallic equips customers with deep visibility and control over backup environments to help ensure data remains safe and recoverable. Metallic offers best practices and additional capabilities for customers to harden their tenants using advanced anomaly detection, workflow authorization, and detailed audit and event logs which can be sent to a location of their choice. Built-in insights and tools help identify the current security posture of customer tenants and provides recommending actions for improving, spots malicious files and activities in datasets, suggests pre-infected recovery points for compromised files, and more. Additionally, Metallic offers early warning detection capabilities, capable of flagging zero-day and unknown threats in production environment so businesses can surface advanced attacks which silences bypass security controls – before its time to recover.
At the dawn of this new cyber era, security will remain a team sport – and must be a cornerstone component of any technology investment.
As it relates to data protection, and its increasingly important role in cyber defense and recovery, Commvault and Metallic have made significant platform investments to ensure customer data remains safe, compliant, and recoverable from threats. For more information on Metallic security posture, please visit the following page.


