Metallic SaaS Security, Privacy & Compliance
Built on industry-proven Commvault technologies, Metallic® offers a unique and hardened approach to data protection and security.
Multi-layered security in the cloud
With built-in zero-trust security protocols, Metallic meets the most stringent confidentiality, integrity, and availability standards for government agencies and business, alike.
Security Threat Detection, Protection, and Response
Foundational detection, protection, and response services
- SIEM
- Infrastructure Firewalls, Web Application Firewalls (WAFs)
- IDS (Intrusion Detection System)
- IPS (Intrusion Prevention System)
- Proactive, AI based Incident Response Management
- NDR (Network Detection and Response)
- EDR (Endpoint Detection and Response)
- DDoS Protection (Distributed Denial of Service attack
- End-to-end service monitoring
Zero-trust authentication
Stringent user authentication protocols
- Role Based Access (RBA) controls
- Multi-factor Authentication (MFA)
- FIPS 140-2 certified hardware tokens for MFA
Zero-trust access
Hardened controls, to prevent unwanted access
- Role Based Access (RBA) controls
- Privileged identity management
- Workflow based reviews and approvals
- Automated user behavioral tracking, auditing and management
Virtual air-gap
Preservation of data backups and recovery services
- Independent cloud-based architecture
- Isolated backup copies
- Decoupled backup architecture
- Dedicated secured storage containers
- Separate security domain – outside customer and Commvault network
- Data-in-transit encryption
Immutability
Robust controls to prevent data tampering
- AES 256-bit Dual Data-at-Rest encryption
- Privacy locks
- Read-only rights
- Multi-authorization workflows
- Deletion protection
Advanced Detection
Tools and insights to identify and remediate risks
- Security Posture Score
- Anomaly Detection (File and Data-level)
- Abnormal Event Monitoring and incident management
- User audit trails
Foundational detection, protection, and response services
- SIEM
- Infrastructure Firewalls, Web Application Firewalls (WAFs)
- IDS (Intrusion Detection System)
- IPS (Intrusion Prevention System)
- Proactive, AI based Incident Response Management
- NDR (Network Detection and Response)
- EDR (Endpoint Detection and Response)
- DDoS Protection (Distributed Denial of Service attack
- End-to-end service monitoring
Stringent user authentication protocols
- Role Based Access (RBA) controls
- Multi-factor Authentication (MFA)
- FIPS 140-2 certified hardware tokens for MFA
Hardened controls, to prevent unwanted access
- Role Based Access (RBA) controls
- Privileged identity management
- Workflow based reviews and approvals
- Automated user behavioral tracking, auditing and management
Preservation of data backups and recovery services
- Independent cloud-based architecture
- Isolated backup copies
- Decoupled backup architecture
- Dedicated secured storage containers
- Separate security domain – outside customer and Commvault network
- Data-in-transit encryption
Robust controls to prevent data tampering
- AES 256-bit dual encryption
- Privacy locks
- Read-only rights
- Multi-authorization workflows
- Deletion protection
Tools and insights to identify and remediate risks
- Security Posture Score
- Anomaly Detection (File and Data-level)
- Abnormal Event Monitoring and incident management
- User audit trails
Security Whitepaper Resources
Whitepaper
Metallic® Backup Security & Compliance Overview

Whitepaper
Metallic® ThreatWiseTM Security & Compliance Overview
Industry Standards and Certifications

InfoSec Registered Assessor Program
Australian security assessment framework for systems, services, and applications.
CJIS
Provides data security standards for organization handling criminal justice and law enforcement-centric data.
FedRAMP® High Authorized
The most stringent confidentiality, accessibility, and availability standards set forth for US government contractors and agencies.
See Commvault Cloud for Government for more information.
FIPS 140-2 Compliant
Validates cryptographic modules for encryption and document processing for handling sensitive data.
GDPR
Sets guidelines for the collection and processing of personal information and data.

HIPAA Compliant
Regulates the use and disclosure of protected health information, preventing unauthorized use or theft of sensitive patient data.
ISO Certified
Establishes international standards for managing risks to the security of information.

PCI Certified
Provides security standards and criteria for the acceptance, processing, storage, and transmission of credit card information.
.
SOC 2: Type II Certified
Assesses ability to meet overall security policies, including availability, processing integrity, confidentiality, and privacy standards.
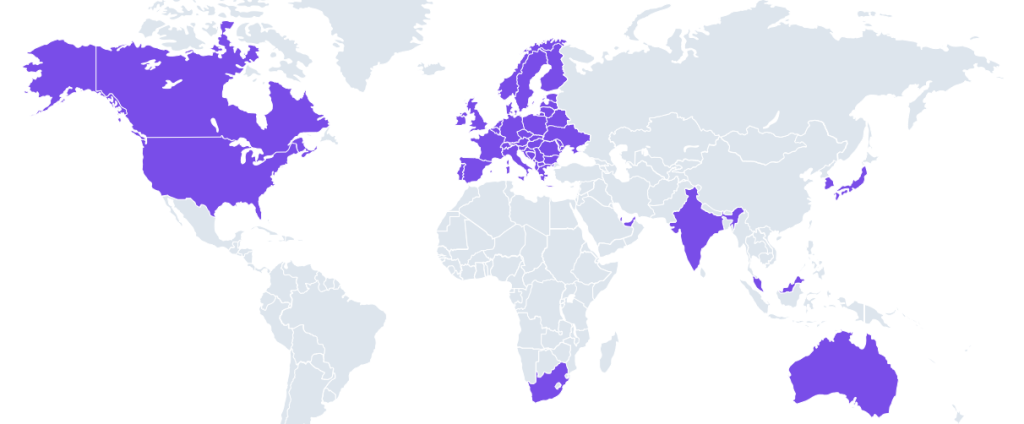
Data Sovereignty
To help global businesses fulfill their data residency and compliance requirements, Metallic customers have full control over where their data lives and can select one (or more) Azure data centers and associate users to that region.
Regions supported by Commvault Cloud
Proven Protection. No compromises.
See why our customers trust us to enable secure experiences
Safeguard your data
Metallic is committed to supporting our customer’s compliance with GDPR, and prioritizes the privacy and security of the data we protect with our entire product suite.
Future-proof protection – for better peace of mind
Zero-trust security to safeguard endpoints, SaaS applications,
and hybrid cloud environments – now and in the future
Metallic Government Cloud
The ONLY FedRAMP High In Process – In PMO Review DPaaS solution, for federal agencies and government contractors
Security & Ransomware Blogs

Blog
Ransomware Cybersecurity

Blog
Active Directory Ransomware-recovery

Webinar
New Security Tools & Insights from Metallic
FAQs
Yes. Metallic has a comprehensive security program. We embed security best practices across all our technology, programs and processes with a defense-in-depth approach including but not limited to:
- Security awareness and training to all employees
- Data center, host and network security
- Infrastructure logging and monitoring
- Secure infrastructure access, identification and authentication
- Security Risk Management
- Data Privacy
- Secure Development lifecycle
- Threat intelligence, detection and incident response
Metallic has implemented an end-to-end DevSecOps program for Metallic Security Management. The Metallic DevSecOps program covers all aspects of Metallic Security Posture such as
- Proactive cloud infrastructure and platform vulnerability management
- End-to-end proactive threat monitoring and response through centralized SecOps center
- Access management and controls
Metallic follows security controls and guidelines based on NIST 800-53 to protect information systems and cloud infrastructure. The broad set of controls provide are part of Metallic’s comprehensive security program.
Metallic uses OWASP Top-Ten standard for secure software development and performs vulnerability scanning along with dev, test, QA, and pre-production step-based code release for thorough security and service stability validation.
Yes. All data flow across the Metallic service is transmitted over TLS 1.3 links and stored at-rest with dual AES 256 bit encryption.
Metallic has a fully documented business continuity and disaster recovery plan. It is managed through the Metallic DevSecOps program and in compliance with the security and compliance certifications obtained by Metallic, including SOC 2 type II, ISO27001:2013, FedRAMP High In Process – In PMO Review and others.
Yes, Metallic tests its business continuity and disaster recovery plans periodically. Test plans and results are validated and certified by a third party assessor as required by multiple security and compliance certification programs.
Security Notices and Alerts
Stay up-to-date on the latest incidents and alerts
With the recent discovery of the Log4j vulnerabilities as disclosed in CVE-2021-44228, CVE-2021-45046, CVE-2021-45105, the Metallic team has performed an extensive security assessment and threat analysis.
We have found that the Log4j vulnerability has no impact on Metallic or the security and privacy of your data backups. Metallic does not use the impacted libraries as per the advisories.
We will continue to proactively monitor and provide any further updates, while customers with questions can reach out to Metallic.io/support.
Updated December 23, 2021
With the recent announcement of the Volt Typhoon cyber campaign, as disclosed by Microsoft on May 24, 2023, our team has conducted a thorough security assessment of Commvault and Metallic services.
Upon our evaluation, we have found no impact to the security, privacy, or integrity of your data backups.
Commvault and Metallic solutions employ a multi-layered and zero-trust architecture, which include necessary controls to address this vulnerability.
Moving forward, we recommend that customers follow all Microsoft recommendations to address and defend against this cyber campaign.
We also recommend that customers check their Commvault and Metallic environment to ensure security controls such as the following are active:
- MFA is properly configured and up to date
- Dual authorization workflows are in place for backup and restore operations
- Compliance locks are enabled for services, apps, and backup destinations
- Additionally, for customers looking for an extra layer of protection, we encourage you to evaluate ThreatWise, capable of surfacing zero-day and unknown threats in production environments
We will continue to proactively monitor this matter and provide further updates as needed.
Updated May 26, 2023
It’s a good day for a test drive
Advanced security meets data management with Security IQ