Three Essential Capabilities for Ransomware Readiness
Last year alone, nearly 60% of enterprises were hit with a ransomware attack,1 and 73% of cyber attacks resulted in data being encrypted and held for ransom.2 2020 has seen a continued uptick in ransomware attacks with threat actors taking advantage of economic and workplace disruption caused by the Covid-19 outbreak. Given the increasing risks and the severe impact of data loss, organizations should look to implement tooling and processes that detect, prevent and ensure recovery readiness as part of their data protection strategy. The right cloud storage approach plays a significant role.
Cloud Storage as Backup Target
Securely storing backup copies of your critical data is a must-have for defending against malicious attacks. After all, more than half of organizations that did recover their data from ransomware did so from back-up copies.2 The traditional 3-2-1 data protection strategy recommends: 3 copies, 2 media types, 1 off-site location. Implementing this strategy in the physical world often means cumbersome media and long restore times, and the overhead of managing and maintaining on-prem copies also make it cost prohibitive in some cases. A better alternative is to consider using cloud storage as a backup target.
Beware though, all cloud backup isn’t created equal. Latest statistics say nearly 60% of attacks where data was encrypted involved data stored in the public cloud.2 Of course, “public cloud” could mean anything from file storage and sharing solutions like Google Drive and Dropbox to cloud-based backup solutions. The important take-away is that malicious threat actors are targeting cloud data, and the cloud’s shared responsibility model means that its up to the data owners to implement appropriate security checks to protect their data. Access controls, data encryption in flight and at rest, network segmentation, isolation, monitoring for suspicious activity, and immutability are all important mechanisms to secure your cloud copies.
Beyond simply having a copy of your data in the cloud, companies need to consider how their data protection solution provides detection, prevention, as well as recovery readiness.
A comprehensive “cloud shield” against ransomware should include these essential capabilities:
1. Detection – Modern security measures driven by advanced algorithms and machine-learning are better-suited to detect suspicious activity that can presage an attack on your data.
2. Prevention – Any access of your cloud backup data should go through increased scrutiny and additional security measures. Zero trust restrictive access controls can prevent unauthorized access and modifications to data, while encryption all the way and at rest and secure key management are needed for an extra layer of security.
3. Recovery readiness – And lastly, air gapped cloud copies are a must. Immutable copies of your data with object locks guard against malicious attack, while offline copies with the ability to shut down connectivity can contain an attack quickly.
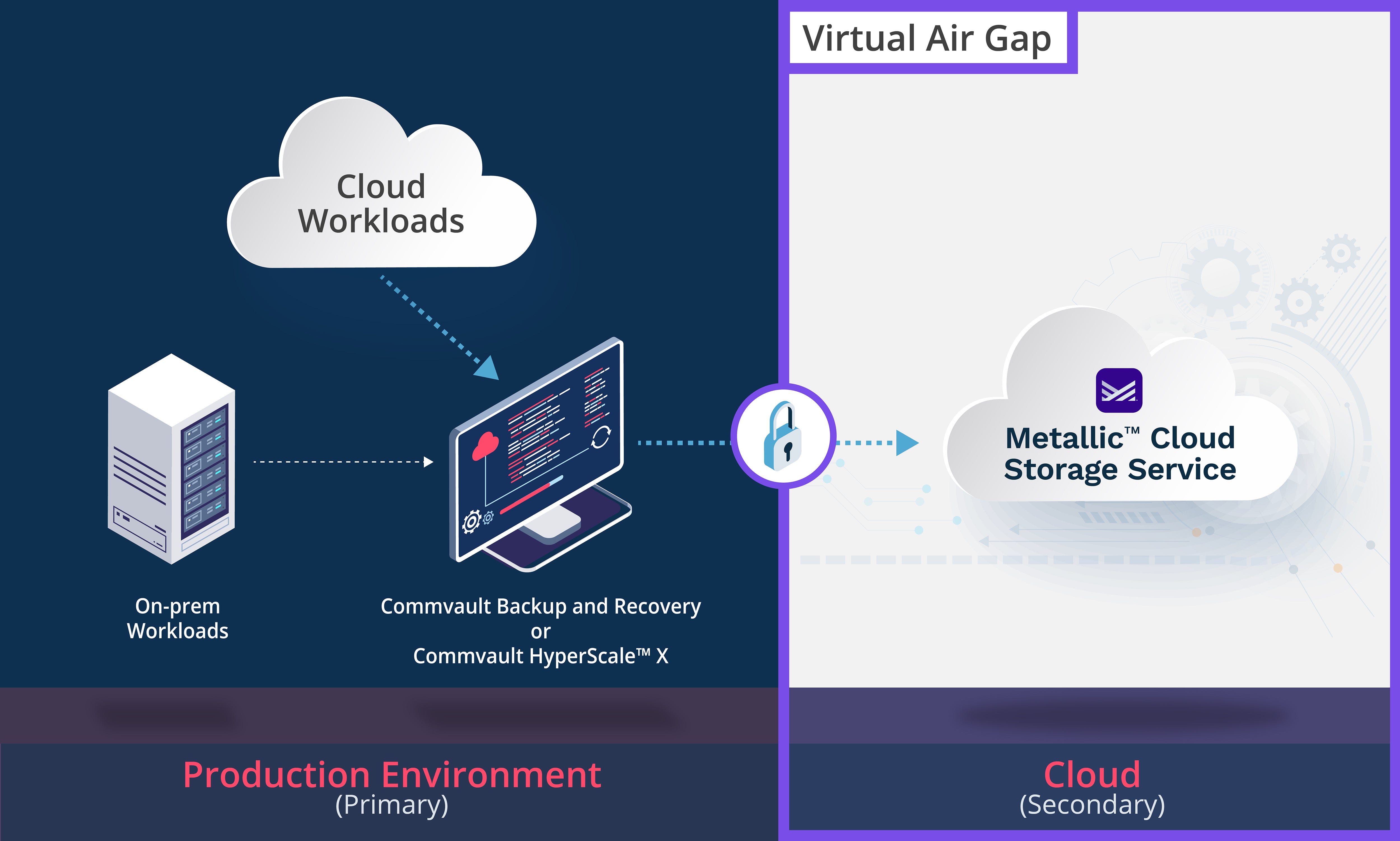
Metallic Cloud Storage Service
In addition to the Metallic SaaS offerings that deliver against these capabilities, we’ve just introduced Metallic™ Cloud Storage Service for customers running Commvault Backup & Recovery software or HyperScale™ X appliance. Created as an “easy button” to cloud storage adoption, this managed cloud storage service provides a secure, cost effective, modern alternative for adhering to the 3-2-1 rule of data protection with the unmatched technology of Commvault + Metallic SaaS, built on Microsoft Azure. Layered security best practices are baked-in to shield and protect organizations’ critical data. With Metallic Cloud Storage Service, Commvault customers can:
- Monitor anomalous backup changes such as backup size and file activity changes. Anomalies detected in backups help administrators identify potential indicators of ransomware or other threats. File system metrics, modifications and deletions are also monitored by Commvault’s backup agents that provide another level of detection capabilities.
- Utilize built-in security access controls and encryption to prevent unauthorized access and mitigate ransomware risk. Commvault + Metallic leverages security controls such as multi-factor authentication for everyday administrative tasks, privacy locks, and data encryption. Zero-trust controls help limit internal lateral movement to prevent data loss and unauthorized access to data.
- Store virtually air gapped copies with immutability options outside of customer accounts for protection against accidental or malicious threat actors. Isolating data targets through network segmentation reduces the likelihood of ransomware or unauthorized threat actors gaining access to backups. TLS encrypted one-way secure tunnels can be used to secure storage targets. Air gapping controls within the solution include the ability to turn off connectivity to the data stores when not needed, effectively severing the data path.
- Mitigate risk using Metallic Cloud Storage Service’s hardened infrastructure built on Azure Blobs with multi-layered security and monitoring operations powering the service. Metallic SaaS is ISO27001, GDPR and SOC 2 compliant and encrypts all data and metadata traversing through the network and at rest while enforcing secure access controls.
Simply put—Metallic Cloud Storage Service delivers critical tooling and capabilities essential to effectively combat ransomware threats for organizations using Commvault’s on-premises backup software and/or appliance. Companies leveraging Metallic Cloud Storage Service as a backup target benefit from additional layers of security, and incorporating it as an integral part of their data ptotection strategy will position them well for guarding against attacks.

References:
1 ESG. Technology Spending Intentions, Feb 2020
2 Sophos. The State of Ransomware, May 2020


